Chacha20
ChaCha20-Poly1305 is almost 3 times faster than AES when the CPU does not provide dedicated AES instructions. Its dangerous to use something so low-level.

Silex Insight Unveils New Version Of Chacha20 Poly1305 Authenticated Encryption Dsp Valley
Intel processors provide AES-NI instruction set.
Chacha20. Package chacha20 implements the ChaCha20 and XChaCha20 encryption algorithms as specified in RFC 8439 and draft-irtf-cfrg-xchacha-01. Poly1305 also saves network bandwidth. The ChaCha20 stream cipher.
Chacha works great in general purpose CPUs and takes advantage of SIMD which exists on virtually all non-embedded CPUs and is hard to fuck up. ChaCha20 AVX2 implementation had a bug related to carries. Similar to AES-CTR ChaCha20 is a stream cipher.
This class implements the ChaCha20 stream cipher as specified by RFC 7539. So in a way and from the perspective of a programmer its not secure at all. The Salsa20 directory in version 20080120 of the eSTREAM benchmarking suite includes several implementations of ChaCha8 and ChaCha12 and ChaCha20.
The ChaCha20 algorithm is a stream cipher using a key of 256 bit size. The bug was fixed in Crypto 86. Mbedtls_chacha20_setkey and mbedtls_chacha20_starts must be called at least once to setup the context before this function can be called.
ChaCha20 and Poly1305-AESIt was inspired by a similar proposal for TLS which seems to have actively been backed by Google in the recent months. Note The input and output pointers must either be equal or point to non-overlapping buffers. What does this protocol mean for SSH.
ChaCha20-Poly1305 is three times faster than AES-GCM on devices that dont have AES hardware acceleration. The bug appeared to be relatively rare when the cpu had AVX2 and it did not appear in other implementations like SSE or NEON. ChaCha20 is a primitive in other words its just one component of a secure cryptographic system and PyCryptodome is a collection of primitives.
RFC 7539 ChaCha20 Poly1305 May 2015 1Introduction The Advanced Encryption Standard AES -- has become the gold standard in encryptionIts efficient design widespread implementation and hardware support allow for high performance in many areas. ChaCha20 has a considerably bigger safety margin. This package provides implementations of three ChaCha versions.
ChaCha20 is based upon an earlier cipher developed by DJB called Salsa that dates back to 2005 and was submitted to the eSTREAM competition. The most common ChaCha variant is ChaCha20 20 rounds. ChaCha20 itself was published in 2008.
XChaCha20 is a variant of ChaCha20 with an extended nonce allowing random nonces to be safe. It is a variant of Salsa20 with better diffusion. ChaCha20 doesnt require any lookup tables and avoids the possibility of timing attacks.
The ChaCha20 cipher and. Ref a reference implementation. Similar to ref but uses separate temporary variables instead of a temporary array.
ChaCha20 562 API Documentation javalangObject. XChaCha20 doesnt require any lookup tables and avoids the possibility of timing attacks. ChaCha20 is a stream cipher developed by Daniel J.
This paper presents the ChaCha family and explains the differences between Salsa20 and ChaCha. ChaCha20 AVX2 implementation had a bug related to carries. The bug was fixed in Crypto 86.
Its original design expands a 256-bit key into 264 randomly accessible streams each containing 264 randomly accessible 64-byte 512 bits blocks. On occasion the tail of the cipher text would be incorrect. However because of the large scale of the data it takes a considerable amount of time to encrypt and decrypt them.
ChaCha20 with a 64 bit nonce can endecrypt up to 264 64 bytes for one key-nonce combination. ChaCha20-Poly1305 does not need the nonce to be unpredictable random unlike the IV of AES-GCM. For example in Too Much Crypto the authors recommend 11 instead of 14 for AES-256 and 8 rounds instead of 20 for ChaCha as safe.
On occasion the tail of the cipher text would be incorrect. But most SSH installations are inherently different from TLS. Also see Issue 1069 and Commit 20962baf4440.
Cloudflare introduced the ChaCha20-Poly1305 cipher suite in February 2015 and immediately noticed performance benefits. Since ChaCha20 is a stream cipher the same operation is used for encrypting and decrypting data. It slightly modifies the Salsa round and the number 20 indicates that it repeats for 20 rounds in total.
ChaCha is a stream cipher family created by Daniel J. ChaCha12 and ChaCha20 are analogous modifications of the 12-round and 20-round ciphers Salsa2012 and Salsa2020. Also see Issue 1069 and Commit 20962baf4440.
Data have always been the most valuable asset of enterprises and research institutions and their confidentiality especially the input and output data related to applications running on remote supercomputers should be protected as much as possible. Internally XChaCha20 works like a block cipher used in counter mode. Thus the overhead for running pseudo random number generator can be avoided.
ChaCha20 is standardized in RFC 7539. The bug appeared to be relatively rare when the cpu had AVX2 and it did not appear in other implementations like SSE or NEON. On most modern platforms AES is anywhere from four to ten times as fast as the previous most-used cipher Triple.
1 Introduction 11 Background The Salsa2020 stream cipher expands a 256-bit key into 264 randomly accessible. Public class ChaCha20 extends javaxcryptoCipherSpi.

Chacha20 H File Reference Api Documentation Mbed Tls Previously Polarssl

Chacha20 Poly1305 Cipher Summary Adalabs Sparkada Openssh Ciphers

4 Authenticated Encryption Real World Cryptography

Google Online Security Blog Speeding Up And Strengthening Https Connections For Chrome On Android

Chacha20 Poly1305 Crypto Engine Ip Core

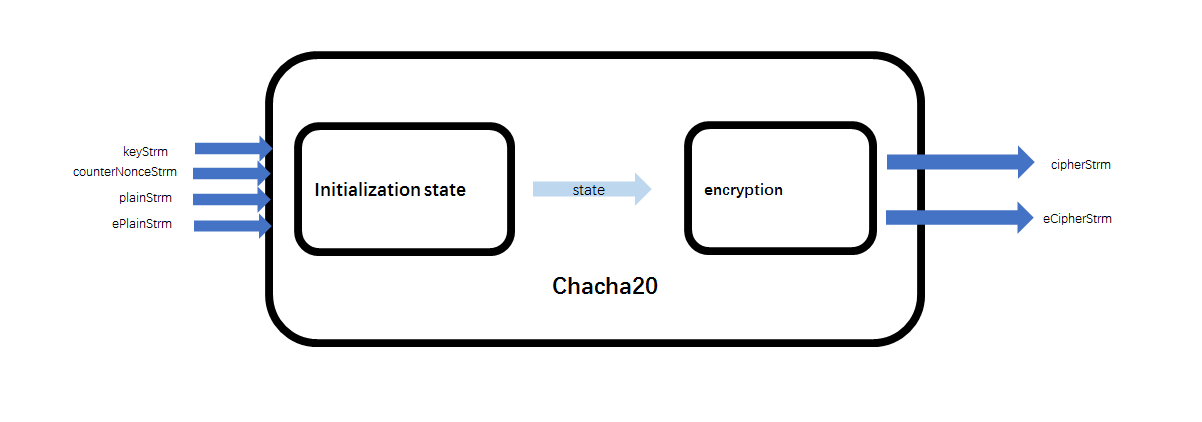
Chacha20 Algorithm Block Diagram Download Scientific Diagram
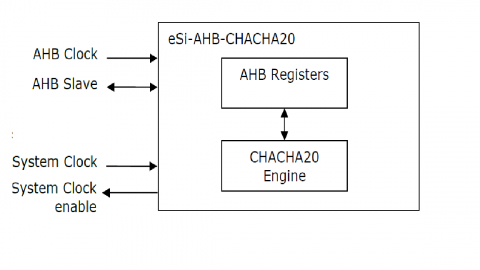
Chacha20 Stream Cipher Core With Ahb Interface

Chacha20 Algorithm Block Diagram Download Scientific Diagram
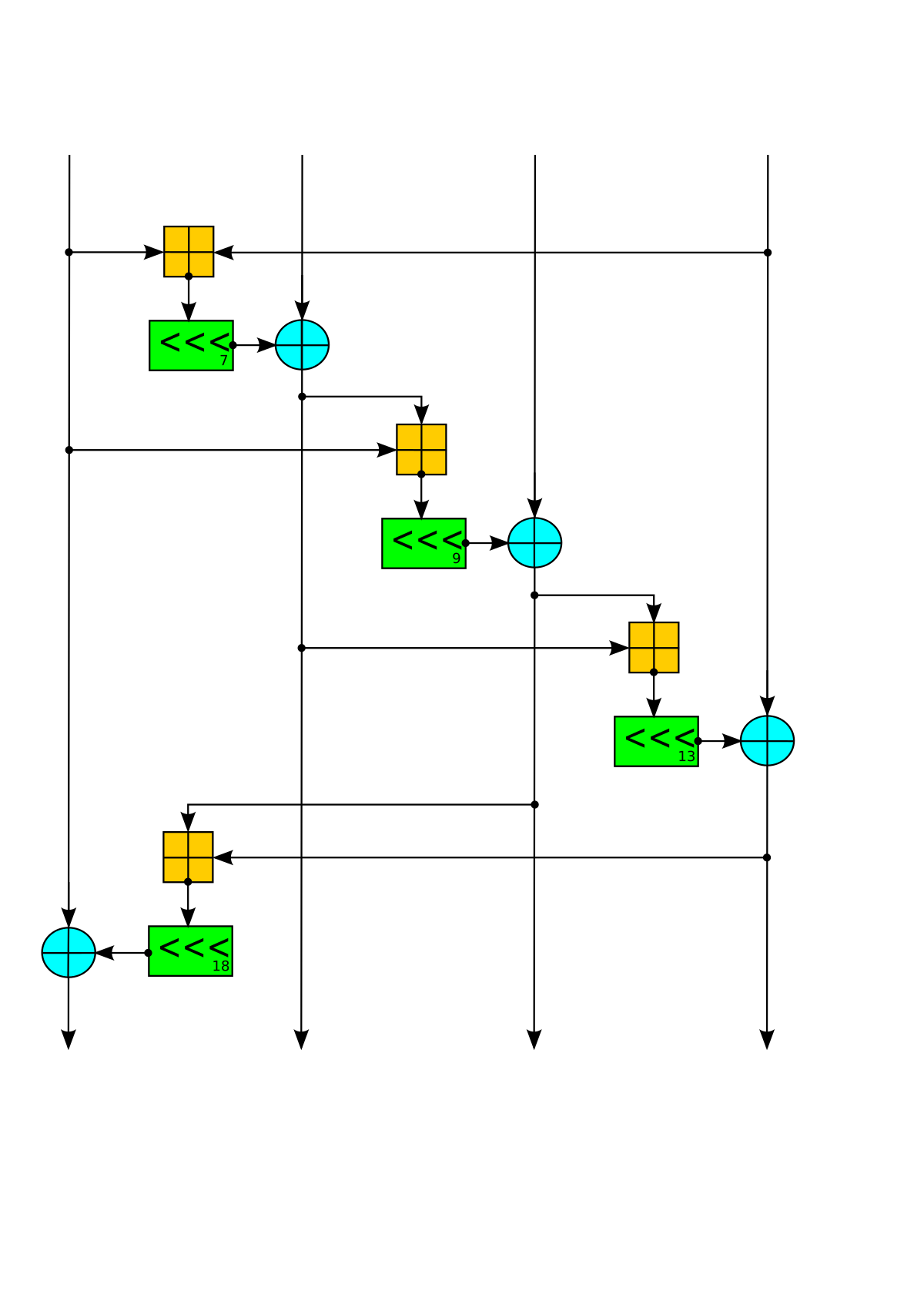
File Chacha20 Diagram Svg Wikimedia Commons

Java Chacha20 Poly1305 Encryption And Decryption Example

Google Online Security Blog Speeding Up And Strengthening Https Connections For Chrome On Android

Chachapoly H File Reference Api Documentation Mbed Tls Previously Polarssl